ESET Research discovers new Chinese threat group: GhostRedirector manipulates Google, poisons Windows servers with backdoors
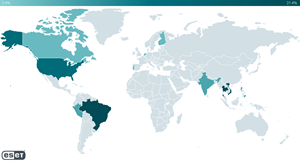
- ESET Research observed at least 65 Windows servers compromised, based on an internet scan from June 2025.
- ESET believes that a previously unknown, China-aligned threat actor is likely behind these attacks. It has been named GhostRedirector by ESET researchers.
- The victims are located mainly in Brazil, Thailand, Vietnam, and the United States.
- The victims are not related to a single specific sector but represent a variety sectors, including insurance, healthcare, retail, transportation, technology, and education.
- GhostRedirector has developed a new C++ backdoor, Rungan, which is capable of executing commands on the victim’s server.
- GhostRedirector has also developed a malicious native IIS module, Gamshen, that can perform Search Engine Optimization (SEO) fraud.
BRATISLAVA, Slovakia, Sept. 04, 2025 (GLOBE NEWSWIRE) -- ESET Research has discovered a new threat actor, which it has named GhostRedirector. In June 2025, this threat actor compromised at least 65 Windows servers, mainly in Brazil, Thailand, Vietnam, and the United States. Other victims were located in Canada, Finland, India, the Netherlands, the Philippines, and Singapore. GhostRedirector used two previously undocumented, custom tools: a passive C++ backdoor that ESET has named Rungan, and a malicious Internet Information Services (IIS) module it has named Gamshen. GhostRedirector is very likely a China-aligned threat actor. While Rungan has the capability of executing commands on a compromised server, the purpose of Gamshen is to provide SEO fraud as-a-service to manipulate Google search engine results, boosting the page ranking of a configured target website. Its purpose is to artificially promote various gambling websites.
“Even though Gamshen only modifies the response when the request comes from Googlebot — i.e., it does not serve malicious content or otherwise affect regular visitors of the websites — participation in the SEO fraud scheme can hurt the compromised host website’s reputation by associating it with shady SEO techniques, as well as with the boosted websites,” explains ESET researcher Fernando Tavella, who made the discovery.
Besides Rungan and Gamshen, GhostRedirector also uses a series of other custom tools, in addition to the publicly known exploits EfsPotato and BadPotato, to create a privileged user on the server that can be used to download and execute other malicious components with higher privileges. Alternatively, it can be used as a fallback in case the Rungan backdoor or other malicious tools are removed from the compromised server.
While the victims are located in different geographic regions, most of the compromised servers located in the United States appear to have been leased to companies that are based in Brazil, Thailand, and Vietnam, where most of the other compromised servers are actually located. Thus, ESET Research believes that GhostRedirector was more interested in targeting victims in Latin America and Southeast Asia. GhostRedirector hasn’t shown interest in a particular vertical or sector; instead, ESET has identified victims across multiple sectors, including education, healthcare, insurance, transportation, technology, and retail.
Based on ESET telemetry, GhostRedirector probably gains initial access to its victims by exploiting a vulnerability, likely an SQL Injection. The attackers compromise a Windows server, then download and execute various malicious tools: a privilege escalation tool, malware that drops multiple webshells, or the already mentioned backdoor and IIS Trojan. In addition to the obvious purpose of the privilege escalation tools, they can also be used as a fallback in case the group loses access to the compromised server. Backdoor capabilities include network communication, file execution, directory listing, and manipulating both Services and Windows registry keys.
“GhostRedirector also demonstrates persistence and operational resilience by deploying multiple remote access tools on the compromised server, on top of creating rogue user accounts, all in an effort to maintain long-term access to the compromised infrastructure,” said Tavella.
ESET telemetry detected attacks by GhostRedirector between December 2024 and April 2025, and an internet-wide scan from June 2025 identified further victims. ESET notified all the identified victims it discovered via the scan about the compromise. Mitigation recommendations can be found in our previously published comprehensive white paper.
For a more detailed analysis and technical breakdown of GhostRedirector, check out the latest ESET Research blogpost, “GhostRedirector poisons Windows servers: Backdoors with a side of Potatoes,” on WeLiveSecurity.com. Make sure to follow ESET Research on Twitter (today known as X), BlueSky, and Mastodon for the latest news from ESET Research.
About ESET
ESET® provides cutting-edge cybersecurity to prevent attacks before they happen. By combining the power of AI and human expertise, ESET stays ahead of emerging global cyberthreats, both known and unknown—securing businesses, critical infrastructure, and individuals. Whether it’s endpoint, cloud, or mobile protection, our AI-native, cloud-first solutions and services remain highly effective and easy to use. ESET technology includes robust detection and response, ultra-secure encryption, and multifactor authentication. With 24/7 real-time defense and strong local support, we keep users safe and businesses running without interruption. The ever-evolving digital landscape demands a progressive approach to security: ESET is committed to world-class research and powerful threat intelligence, backed by R&D centers and a strong global partner network. For more information, visit www.eset.com or follow our social media, podcasts, and blogs.
A photo accompanying this announcement is available at https://www.globenewswire.com/NewsRoom/AttachmentNg/352d65d6-ef53-473c-87ae-c28ebf544004

Media contact: Jessica Beffa jessica.beffa@eset.com 720-413-4938
Legal Disclaimer:
EIN Presswire provides this news content "as is" without warranty of any kind. We do not accept any responsibility or liability for the accuracy, content, images, videos, licenses, completeness, legality, or reliability of the information contained in this article. If you have any complaints or copyright issues related to this article, kindly contact the author above.